Network Penetration Testing Methodologies And Standards – A methodology is a system of methods that are used in a particular area of study or activity. In terms of penetration testing, it’s going to be this systematic approach that we take. When we look at it from the PenTest+ perspective, there are four steps in the pentest methodology.
Pentest Methodology
- The first step is planning and scoping.
- The second step is information gathering and vulnerability identification.
- The third step is attacking and exploiting the target.
- The fourth step is reporting and communicating.
Also Read: IT Security Governance And Responsibilities – CompTIA Security
You’ll notice that matches up with domains one, two, three, and five of the PenTest+ exam because that is the methodology that CompTIA is going to use. But it’s not the only penetration testing methodology out there. Penetration Testing Methodologies
Ethical Hacker Methodology
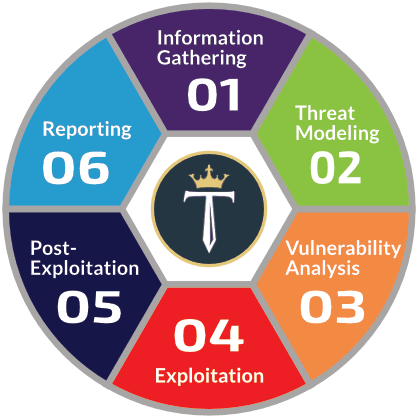
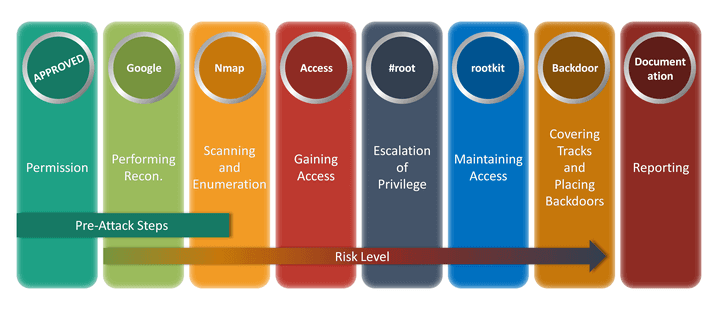
In fact, if you’ve taken the certified ethical hacker exam, there is what they call the Ethical Hacker’s Methodology. This involves permission, performing reconnaissance, scanning and enumeration, gaining access, escalation of privileges, maintaining access, covering your tracks and backdoors, and reporting.
It moves from left to right. Now, this is a long way of putting it, but it really is the same methodology that we just talked about with PenTest+ because the permission is going to be in the scoping phase. The performing reconnaissance and the scanning and enumeration is going to be phase two. When we get to exploitation, that covers gaining access, escalation of privileges, maintaining access, and covering your tracks and backdoors. Then, finally, we have reporting and communication covered by reporting.
It’s based off of NIST, which is an industry standard that is used all throughout the United States, especially in the federal government and department of defense. So, now that we understand the methodology we’re going to use, let’s start digging in to planning and scoping in much, much more depth.
No Responses