Using Guides And Critical Risk Assessment Cases is a critical part of the I.T. risk management process. Now you’ve got to be careful about this because CompTIA actually approaches this and it what in my opinion is a slightly strange way. When I’m talking about risk assessment I want to be able to say here’s a new router, what are the things that I have to worry about? Or here’s this new version of Windows, what are the things that I need to worry about? For me that’s what risk assessment means. But as you actually looked at the objectives you’ll see what CompTIA is really trying to say is how do we secure stuff.
Benchmark
So one example of a good risk assessment guide would be a benchmark. A company with a router is going to tell you how hard the CPU in that router should be working at any given time. So if it gets above 10 percent that could be an issue, it’s working too hard. We can also do our own benchmarks. For example every operating system has benchmarking tools. And I can run it against a particular host to see what its network throughput is to see how many files per second a storage device is working.
Use threshold value to verify expected throughput or action
And I can use these threshold values to give me an opportunity to know what is supposed to be doing the right thing in any given moment. It’s a guide. But to me what we’re really talking about more than anything else are what I call secure configuration guides.
Secure Configuration
Everything from routers to operating systems to applications to wireless access points all need some form of configuration and we want to configure them securely, so really if you take a look at the objectives for the exam you’ll see that that’s what CompTIA is pushing really really hard. So in particular we’re going to be talking about platform and vendor specific guides. Now what I did is I brought my system up and what I’ve got is a whole bunch of examples of different guides at all these different kinds of levels for us to take a look at.
Also Read: How To Deploy a NGINX Web Server Droplet on Digital Ocean
Also Read: CIA Triad of Security – Risk Management – CompTIA Security
Platform And Vendor Guides
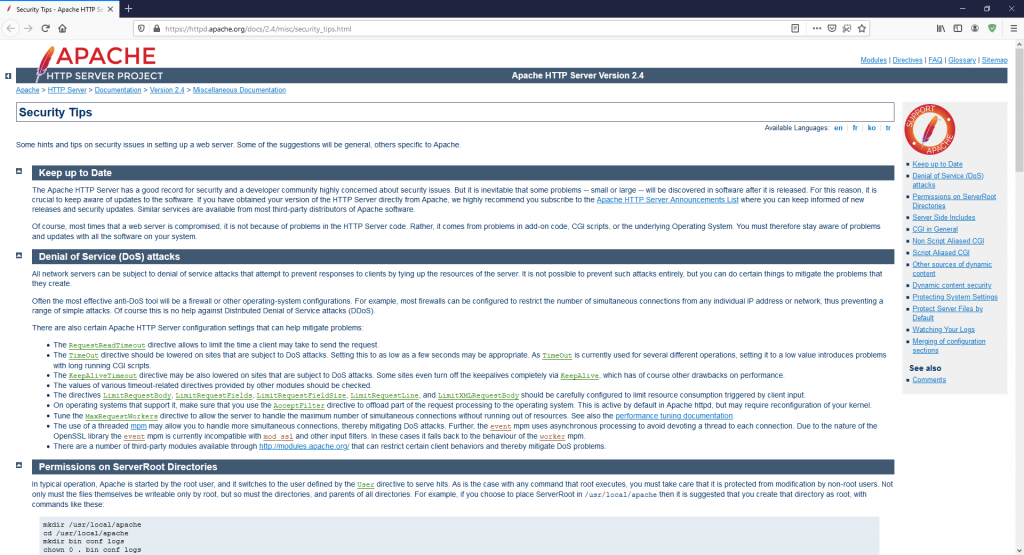
Now the first place I’d like to take a look is under a web server or an application server in this particular case with a web server, if we take a look here on the screen you’ll see I’ve got Apache security tips up and this gives me a bunch of really powerful tools that I like the way Apache does this. It says simple obvious things like keep it up to date. But then it goes into a lot more detail in terms of configurations that we can set up on our web server to make sure that it’s running as best as we possibly can.
Now I’m not going to do just Apache, of course, let’s throw in Windows too. And Microsoft does a great job with putting in all kinds of different guides for us to do different types of security and you can see this thing goes on for days and days and days it’s a wonderful powerful tool Now we don’t want to just stop with application servers and web servers. Another big place that we’re going to run into is operating systems. Now for me because I’m an NIST guy, organizations like NIST provide wonderful tools like for example here’s a big long tool that allows us to know exactly what we need to go through if we’re going to configure OS 10 for our particular system. Critical Risk Assessment
So you know I’m not even going to bother scrolling all the way through this thing would take forever. But NIST does a really good job of showing us what we can do in terms of configuring different operating systems. They’ve got plenty for Windows and Linux in there just as well. Now again I just happened to use an NIST one. I also assure you that every different type of Linux distro will have some type of guide like this for secure configuration. And I guarantee you Microsoft has about 5000 guides to the exact same thing for their operating system. Critical Risk Assessment
Network Infrastructure Devices
Now the other big one is going to be network infrastructure devices: routers, wireless access points, any type of box that you might want to set up and make sure that it’s secure. Now these could be a bit more challenging. Certain organizations like for example Cisco provide pretty good detailed information in terms of if you’ve got a new box, what are you going to have to do to get it configured. Now I’m a big fan of Ubiquiti products for example here at Total Seminars we use them like crazy. So in this particular example we can take a look right here what we’ve got is a beginner’s guide to EdgeRouter. This comes from ubiquity.
This particular organization although they make great products in terms of having really concise guides don’t do as good of a job as say Cisco does but they also have extremely active forums and communities and everybody is talking about setting up a firewall or whatever I might have to be doing to take care of one issue or another they will have the different types of guides I need for my infrastructure devices. But again because I’m an NIST guy here’s a great example of this is SP 800-153.
Most manufacturers have forums and communities to facilitate open discussion.